|
您目前处于:Development
2016-05-11
|
系列文章:Introduction OAuth 2 is an authorization framework that enables applications to obtain limited access to user accounts on an HTTP service, such as Facebook, GitHub, and DigitalOcean. It works by delegating user authentication to the service that hosts the user account, and authorizing third-party applications to access the user account. OAuth 2 provides authorization flows for web and desktop applications, and mobile devices. This informational guide is geared towards application developers, and provides an overview of OAuth 2 roles, authorization grant types, use cases, and flows. Let's get started with OAuth Roles! OAuth Roles OAuth defines four roles:
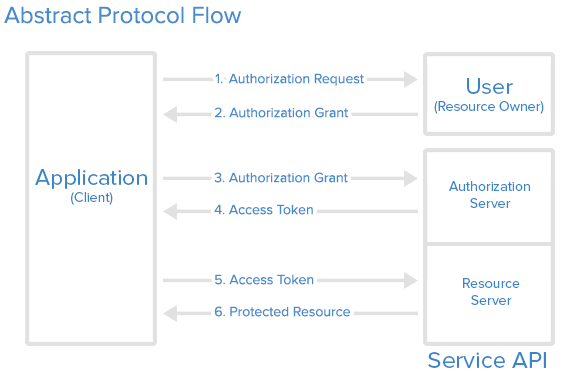
We will detail each role in the following subsections. Resource Owner: User The resource owner is the user who authorizes an application to access their account. The application's access to the user's account is limited to the "scope" of the authorization granted (e.g. read or write access). Resource / Authorization Server: API The resource server hosts the protected user accounts, and the authorization server verifies the identity of the user then issues access tokens to the application. From an application developer's point of view, a service's API fulfills both the resource and authorization server roles. We will refer to both of these roles combined, as the Service or API role. Client: Application The client is the application that wants to access the user's account. Before it may do so, it must be authorized by the user, and the authorization must be validated by the API. Abstract Protocol Flow Now that you have an idea of what the OAuth roles are, let's look at a diagram of how they generally interact with each other:
Here is a more detailed explanation of the steps in the diagram:
The actual flow of this process will differ depending on the authorization grant type in use, but this is the general idea. We will explore different grant types in a later section. Application Registration Before using OAuth with your application, you must register your application with the service. This is done through a registration form in the "developer" or "API" portion of the service's website, where you will provide the following information (and probably details about your application):
The redirect URI is where the service will redirect the user after they authorize (or deny) your application, and therefore the part of your application that will handle authorization codes or access tokens. Client ID and Client Secret Once your application is registered, the service will issue "client credentials" in the form of a client identifier and a client secret. The Client ID is a publicly exposed string that is used by the service API to identify the application, and is also used to build authorization URLs that are presented to users. The Client Secret is used to authenticate the identity of the application to the service API when the application requests to access a user's account, and must be kept private between the application and the API. Authorization Grant In the Abstract Protocol Flow above, the first four steps cover obtaining an authorization grant and access token. The authorization grant type depends on the method used by the application to request authorization, and the grant types supported by the API. OAuth 2 defines four grant types, each of which is useful in different cases:
Reference: https://www.digitalocean.com/community/tutorials/an-introduction-to-oauth-2 转载请并标注: “本文转载自 linkedkeeper.com ” ©著作权归作者所有 |